eSecurity Planet content and product recommendations are editorially independent. We may make money when you click on links to our partners. Learn More. Cyber security
Category: Cloud Security

September 28, 2024 By Sekhar Sarukkai – Cybersecurity@UC Berkeley All signs in the industry point towards rampant growth in the innovation and adoption of AI

During her presentation at the inaugural edition of the InfoQ Dev Summit Munich, Danielle Sudai, security operations lead at Deliveroo, explored the fundamentals of cloud
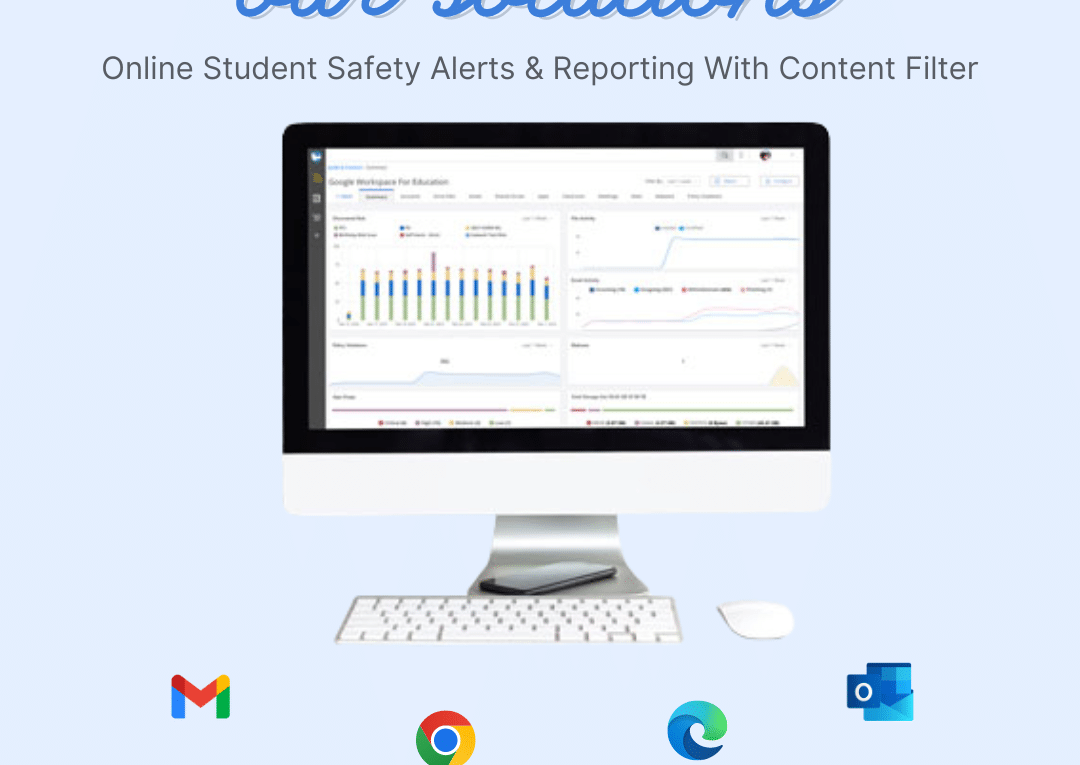
Get Online Student Safety Alerts & Reporting using Content Filter by ManagedMethods As students spend more time on social media and screens, concerns about the
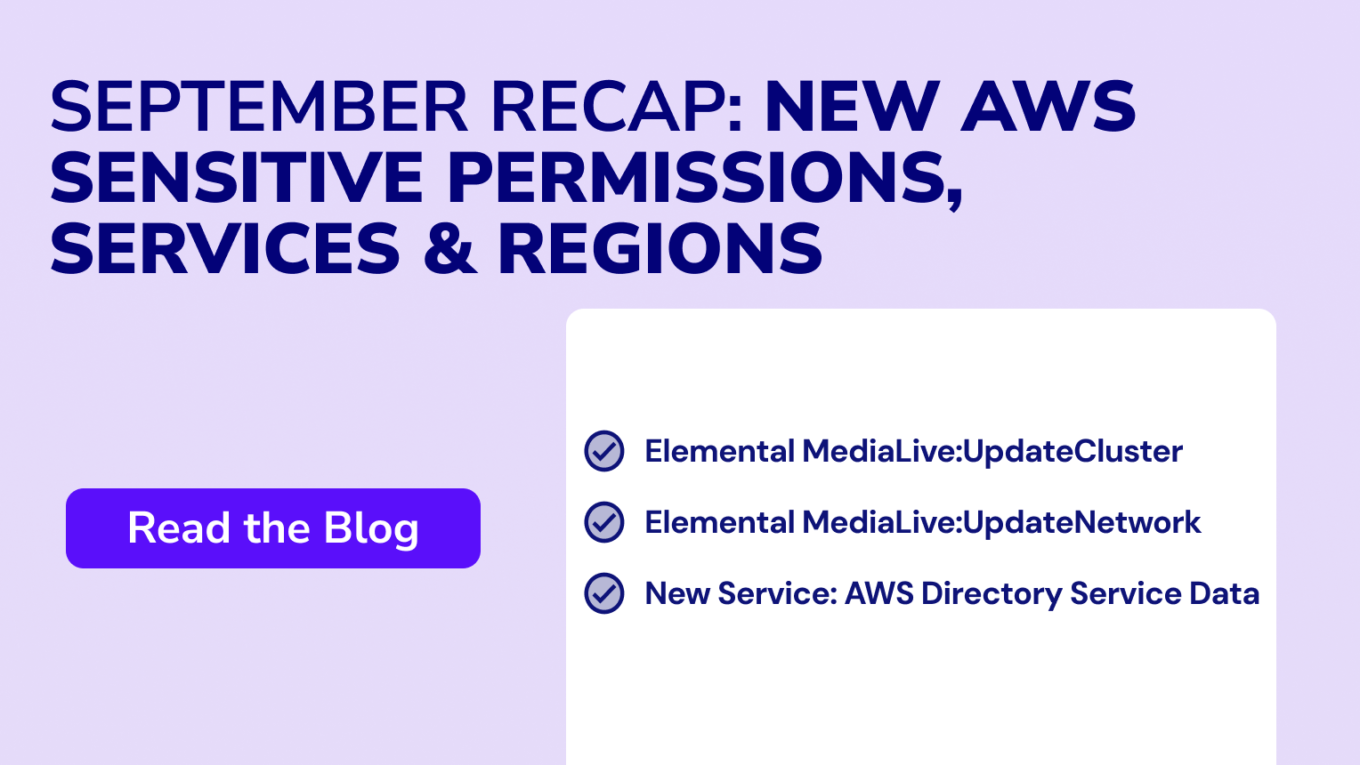
As AWS continues to evolve, new services and permissions are frequently introduced to enhance functionality and security. This blog provides a comprehensive recap of new
Sticking to container security best practices is critical for successfully delivering verified software, as well as preventing severe security breaches and its consequences. These best

eSecurity Planet content and product recommendations are editorially independent. We may make money when you click on links to our partners. Learn More. A cloud

October 3, 2024 By Shubham Jena – Senior Product Manager, Skyhigh Security The world has undergone a massive transformation since the pandemic in 2020, and

Key Takeaways It is important to transition from a reactive to a proactive security posture by dynamically confirming vulnerabilities before applying patches, ensuring security

Technology has seeped its way into every facet of today’s education environment. Students rely on it for their learning, educators for planning and teaching, parents
