In the past, securely managing access to organization resources has been difficult. The only way to gain access has been through an assigned user’s personal
Category: DevOps and Automation

The digital business era is upon us. Enterprises have already made progress in tackling digital transformation and are now transitioning to running viable digital businesses

A Step-by-Step Guide to Safely Rolling out Application Updates using NGINX Ingress in Kubernetes. Executing Canary Deployments Using NGINX Ingress In the world of software

AWSTemplateFormatVersion: “2010-09-09”Description: “Sample template to create an EC2 instance and an S3 bucket.” Parameters:InstanceTypeParameter:Type: StringDefault: t2.microAllowedValues: [t2.micro, t2.small, t2.medium]Description: “Type of EC2 instance to create.”

MySQL Select statement is used in Selecting one or more records in MySQL database, the SELECT statement is being used. Syntax: SELECT * from tableName;

Hey! So, today I want to talk about something that’s absolutely essential if you’re working on any coding project or even just writing documentation for
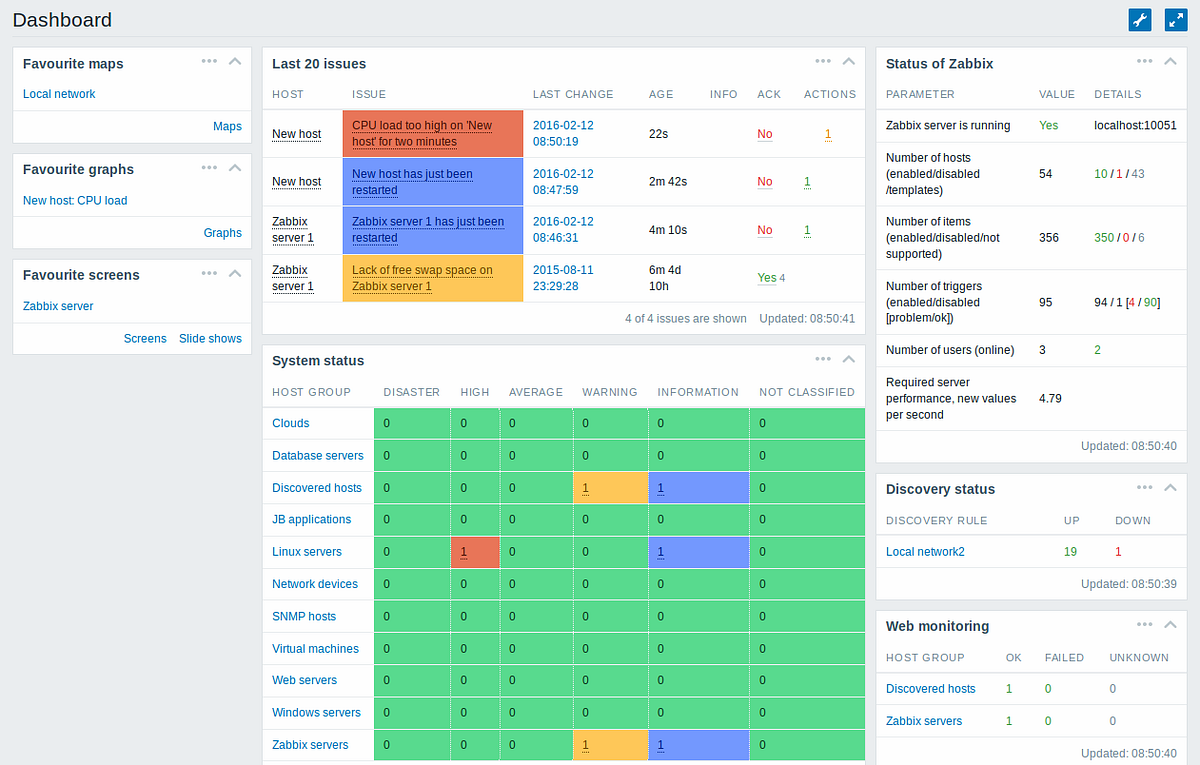
In today’s digital landscape, website availability and performance are crucial for businesses to deliver optimal user experiences. Zabbix, a robust open-source monitoring solution, provides powerful

Pro-Tip: You can also read this post on the MakeWithData Substack for free!https://makewithdata.substack.com/p/practical-terraform-youre-doing-it We’ve all written Terraform IaC that we’re not proud of before —

Building automated CI/CD pipelines, streamlined workflow from development to production. In this detailed tutorial, we will walk through the process of setting up a complete

SQL string functions are useful for manipulating and extracting information from string data in MySQL queries. In this article, we will explore 12 essential SQL
