I recently joined Docker in January as Chief Revenue Officer. My role is responsible for the entire customer journey, from your first interaction with Docker’s
Natural language is rapidly becoming the bridge between human and machine communication. But hallucinations — when a model generates a false or misleading answer —

We’re all familiar with the shared responsibility model championed by cloud providers like AWS, Azure, and GCP: platform providers secure the cloud infrastructure, while customers

Suzie Prince, Head of Product at Atlaasian recently spoke with Abi Noda, CEO at DX, and Andrew Boyagi, Head of DevOps Evangelism at Atlassian, about

Imagine a world where mundane number-crunching tasks are handled automatically, freeing up accountants to focus on strategy and big-picture insights. That world is here, and

Recently, AWS expanded the scope of their AWSCompromisedKeyQuarantine policies (v2 and v3) to include new actions. This policy is used by AWS to lock down

Sonatype today during a virtual All-Day DevOps (ADD) event shared the results of a report that finds there has been a 156% increase in the
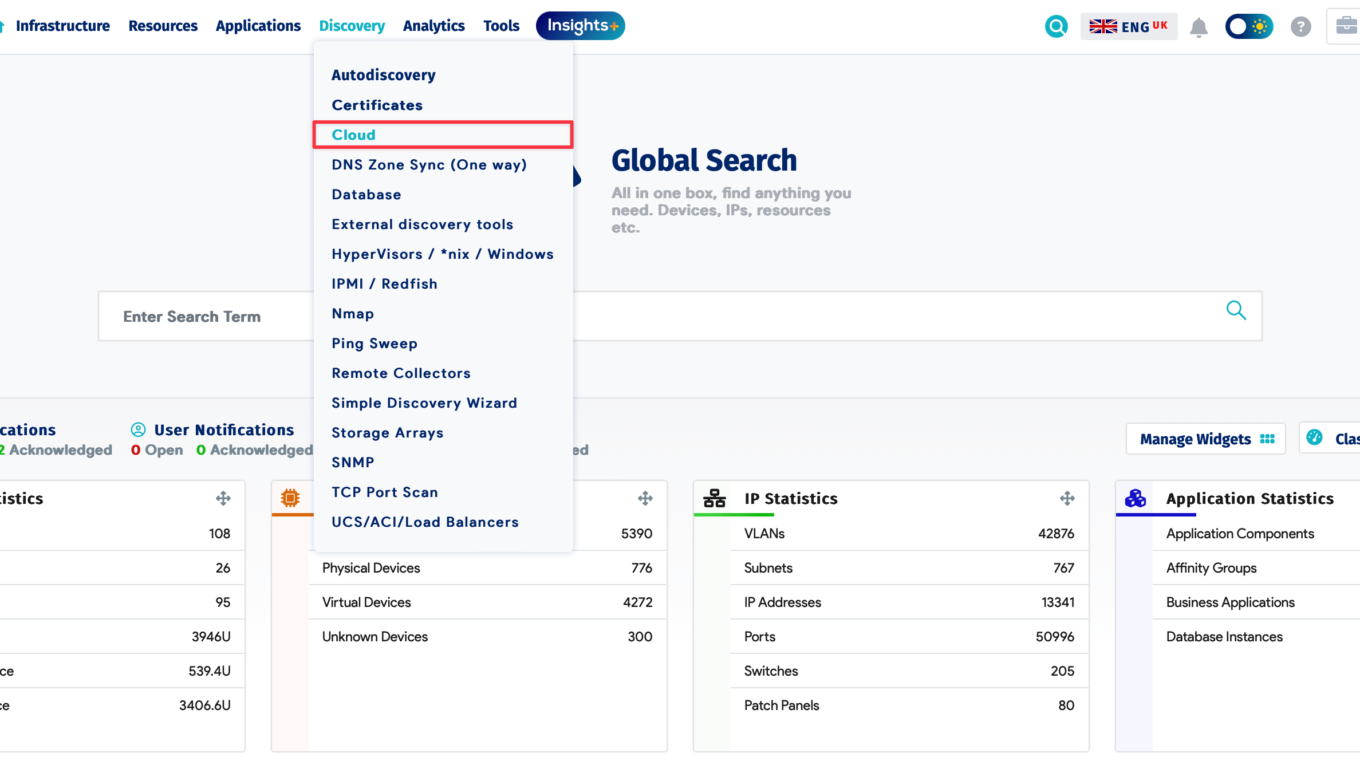
What Is Device42? Device42 is a software solution for IT asset management and data center infrastructure management. It helps organizations keep track of their IT

eSecurity Planet content and product recommendations are editorially independent. We may make money when you click on links to our partners. Learn More. Cyber security

Version managers, in general, are hacks. But they are useful hacks, as they solve a real problem: we all work on multiple projects at the
